By Neil du Plessis | Cloud Security Architect, BUI
The artificial intelligence that powers Copilot for Microsoft 365 is also used in neighbouring Microsoft technologies for the modern workplace. Copilot for Azure, Copilot for Sales, Copilot for Service, Microsoft Copilot Studio, and Microsoft Copilot for Security are either coming soon or already available to Business and Enterprise customers. Let’s take a closer look at each one.
Microsoft describes Copilot for Azure as an AI-powered assistant that simplifies the design, operation, optimisation, and troubleshooting of applications and infrastructure within the Azure ecosystem. It utilises Large Language Models, the Azure control plane, and insights about your Azure and Azure Arc-enabled assets to help you streamline cloud orchestration and management.
Highlights: Copilot for Azure can help you design and develop your cloud applications, choose the best frameworks, languages, and tools, and test and debug your code. It can also help you deploy and manage your applications by providing automation, scalability, and monitoring. In addition, Copilot for Azure can recommend ways to optimise costs and improve security and compliance in your environment.
Availability: Copilot for Azure is currently in preview, and existing Azure customers and Microsoft Partners can apply to participate. If you’re interested, review the registration process before filling in the application form.
Copilot for Sales is designed to help your sales teams boost productivity, improve customer engagements, and close more deals. It takes the foundational capabilities of Copilot for Microsoft 365 and enhances them by connecting to customer relationship management platforms (like Microsoft Dynamics 365 Sales and Salesforce Sales Cloud) and providing sales teams with relevant in-app insights and recommendations to enhance customer interactions.
Highlights: According to Microsoft, Copilot for Sales empowers your sellers to simplify daily tasks, personalise customer interactions, and streamline workflows. From drafting emails in Outlook and setting up meetings in Teams to creating pitch decks in PowerPoint and data visualisations in Excel, Copilot for Sales is geared to help sales teams accomplish more in less time with AI-powered communication, content, and CRM activities.
Availability: Copilot for Sales is available now for $50 per user per month, which includes the requisite Copilot for Microsoft 365 licence. If you already have Copilot for Microsoft 365 (via your Office 365 E3, Office 365 E5, Microsoft 365 E3, Microsoft 365 E5, Microsoft 365 Business Standard, or Microsoft 365 Business Premium subscription), then you can get Copilot for Sales for an additional $20 per user per month. The Copilot for Sales pricing guide has further details, terms, and conditions.
Copilot for Service applies artificial intelligence to your call centre operations to help your customer service and support teams handle customer interactions more efficiently. Copilot for Service brings together all relevant content from your CRM platforms, websites, SharePoint sites, and third-party knowledge bases (like Salesforce, ServiceNow, and Zendesk) and puts it at your agents’ fingertips through conversational AI.
Highlights: Your customer service and support teams can enter natural language prompts and Copilot for Service will generate answers based on your organisational content – from call centre playbooks and user manuals to customer records and case histories in your CRM tools. Your agents can do this in their flow of work during real-time engagements with customers to handle queries faster, resolve issues earlier, and improve customer satisfaction over time.
Availability: Copilot for Service is available now for $50 per user per month, which includes the requisite Copilot for Microsoft 365 licence. If you already have Copilot for Microsoft 365 (via your Office 365 E3, Office 365 E5, Microsoft 365 E3, Microsoft 365 E5, Microsoft 365 Business Standard, or Microsoft 365 Business Premium subscription), then you can get Copilot for Service for an additional $20 per user per month. The Copilot for Service pricing guide has further details, terms, and conditions.
Unveiled by Microsoft at the 2023 Microsoft Ignite conference, Microsoft Copilot Studio is a low-code tool that enables you to tailor Copilot for Microsoft 365 and build your own AI-driven copilots by leveraging conversational features like custom GPTs and generative AI plugins.
Highlights: With Microsoft Copilot Studio, you’re able to personalise Copilot for Microsoft 365 according to your business needs. You can develop, test, and publish standalone copilots and regulate and secure them with the appropriate permissions, data access, and user controls. You can also see the end-to-end lifecycle of your customisations and standalone copilots in one place, which makes building, deploying, managing, and analysing them easier and simpler. In addition, you can use Microsoft Copilot Studio to link Copilot to other data sources to access any system of record, including SAP, ServiceNow, and Workday.
Availability: Microsoft Copilot Studio is available now, and the integration with Copilot for Microsoft 365 is currently in public preview. The Microsoft Copilot Studio website has further details, terms, and conditions.
Microsoft Copilot for Security was also announced at the 2023 Microsoft Ignite conference, where Microsoft explained it as an AI-powered cybersecurity product that “enables security professionals to respond to cyberthreats quickly, process signals at machine speed, and assess risk exposure in minutes”.
Highlights: Microsoft Copilot for Security combines an advanced Large Language Model with a security-specific model informed by Microsoft’s unique global threat intelligence and more than 65 trillion daily signals. The result is a sophisticated, security-focused AI assistant that can provide actionable responses to your natural language questions. These responses can be in the form of text, code, or a visual that helps you understand the full context of a security incident, its impact, and the next steps you should take for remediation and defence hardening.
Availability: Microsoft Copilot for Security is currently in private preview through an invitation-only Early Access Programme for customers and Microsoft Partners. BUI is participating in the Microsoft Copilot for Security Partner Private Preview, and is working with Microsoft product teams to help shape product development. Learn more in our news update.
With Copilot for Azure, Copilot for Sales, Copilot for Service, Microsoft Copilot Studio, and Microsoft Copilot for Security, Microsoft is expanding its range of AI-powered technologies to help you streamline cloud orchestration and management, boost sales productivity, improve customer service, spur innovation, and secure your data and resources. The sooner you start exploring these tools, the sooner you’ll be ready to empower your teams for even greater success.
BUI Cloud Security Architect Neil du Plessis is a certified CISSP and Microsoft Cybersecurity Expert specialising in holistic, cloud-powered defences for modern workplaces.
Wondering if Copilot for Microsoft 365 is right for your organisation? Join the BUI team for an interactive workshop and we’ll assess your Copilot for Microsoft 365 readiness and define a road map for your adoption journey. The workshop is conducted virtually, and is suitable for senior business development managers, line-of-business leaders, managers, technical decision-makers, and end-users. Register your interest by completing this digital form and we’ll contact you directly.
Terms and Conditions for this security vulnerability disclosure blog:
Microsoft Defender XDR is a comprehensive cybersecurity solution designed by Microsoft to protect organisational networks and devices. At its core are the Attack Surface Reduction (ASR) rules, which are strategic security protocols aimed at minimising the vulnerabilities and pathways exploited by cyber threats. These rules act as a crucial line of defence, shielding endpoints from various attack vectors such as malicious documents, scripts, and other potentially harmful activities. However, despite their importance in fortifying cybersecurity defences, recent scrutiny has uncovered a critical vulnerability within these ASR rules. This vulnerability poses a significant risk as it allows adversaries to bypass established security measures without triggering alerts or raising suspicion, thereby compromising the effectiveness of Microsoft Defender XDR’s defence mechanisms.
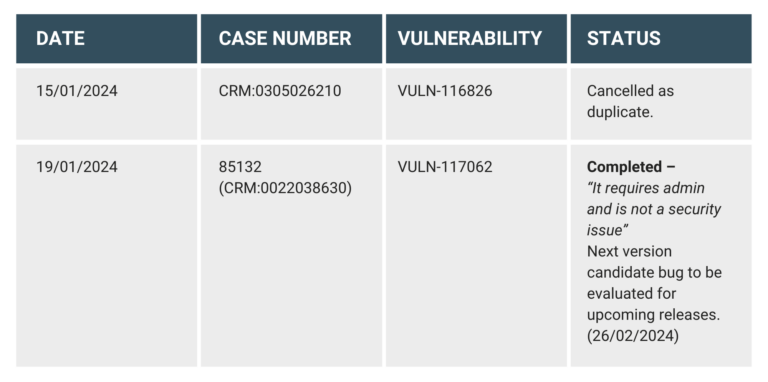
Regrettably, a remedy for this issue is not yet available*. Consequently, recourse to Advanced Hunting queries armed with Custom detection rules becomes imperative to diligently monitor for any indicators of compromise, thereby mitigating potential risks.
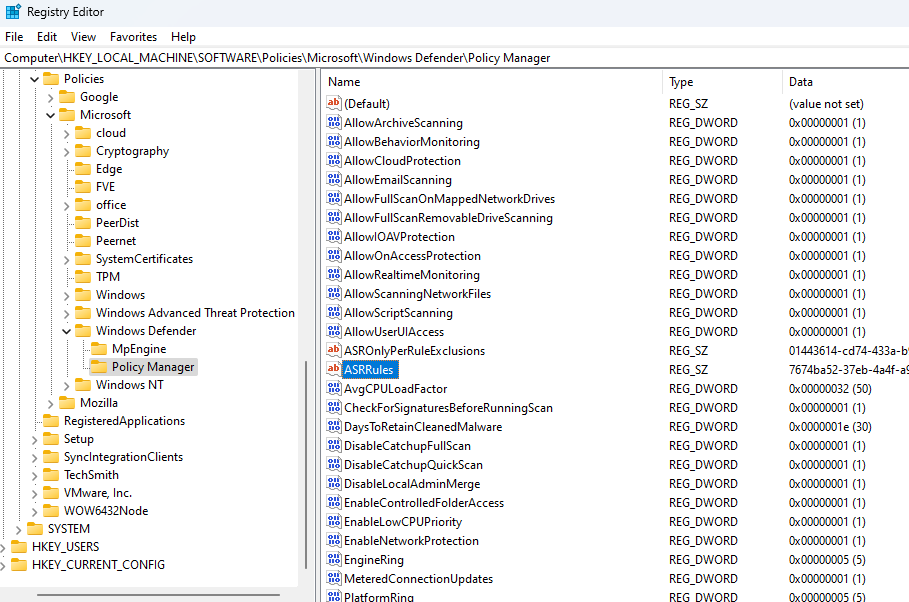
Attack Surface Reduction (ASR) rules are configured on devices by means of a registry key. The contents of this key include the GUID for the specific ASR rule as well as the state of the rule (Block, Audit).
The registry key is not protected and can be modified without triggering any alerts, essentially bypassing ASR rules, which could result in negation of the protection.
Registry Key:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Policy Manager\ASR Rules
By following the steps below, ASR rules can be bypassed. The rule Block all Office applications from creating child processes will be tested.
Bypassing ASR rules:
Get-MpPreference | Select-Object -expandproperty AttackSurfaceReductionRules_Ids
Get-MpPreference | Select-Object -expandproperty AttackSurfaceReductionRules_Actions
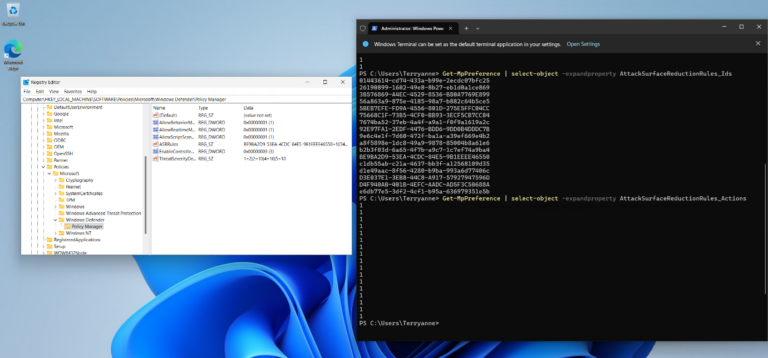
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Policy Manager\
ASR Rules
Get-MpPreference | Select-Object -expandproperty AttackSurfaceReductionRules_Ids
Get-MpPreference | Select-Object -expandproperty AttackSurfaceReductionRules_Actions
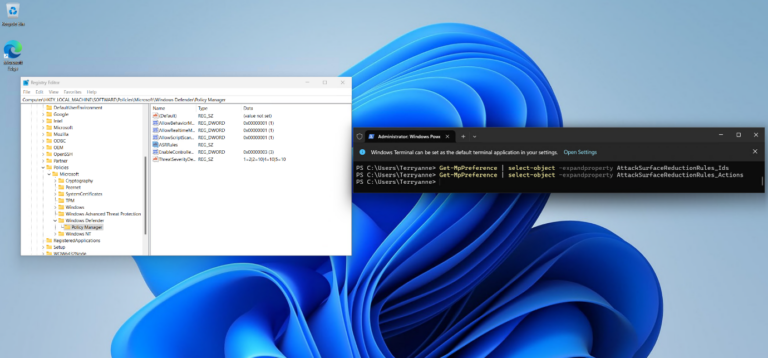
Testing the bypass:
Example: Mkdir “c:\tools\new folder”
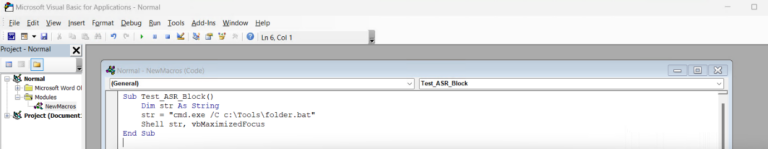
Sub [your Macro name] ()
Dim str As String
Str = “cmd.exe /C [location of bat file] ”
shell str, vbMaximizedFocus
End Sub
Example shown here in screenshot:
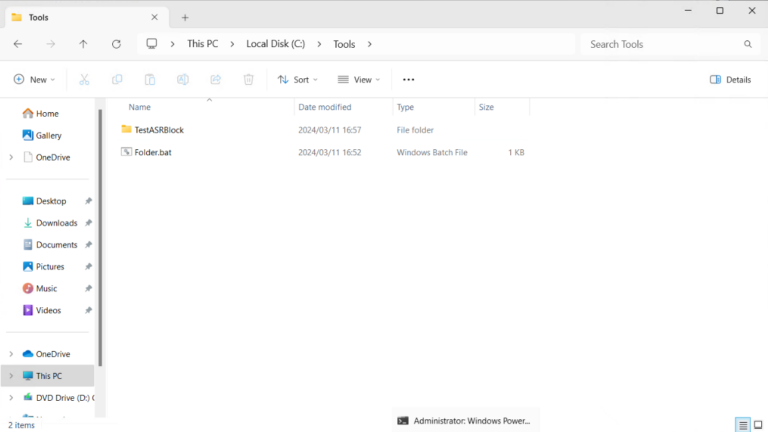
The successful creation of a folder indicates that ASR rules have been successfully bypassed.
Running the same Macro without bypassing the ASR rules results in the following alert:
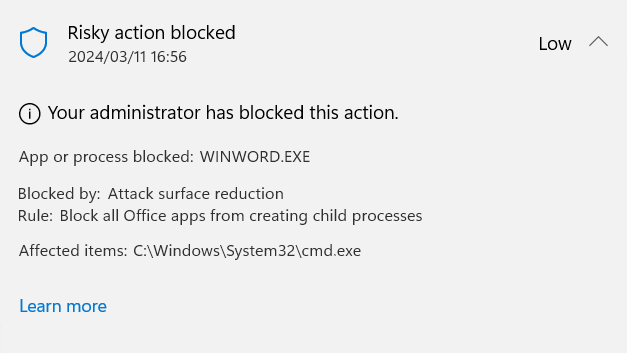
By determining the current ASR policy configuration and monitoring for any changes to this configuration, Advanced Hunting queries with Custom detection rules can act as a potential mitigation strategy until this critical vulnerability is remediated.
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Policy Manager\ASR Rules
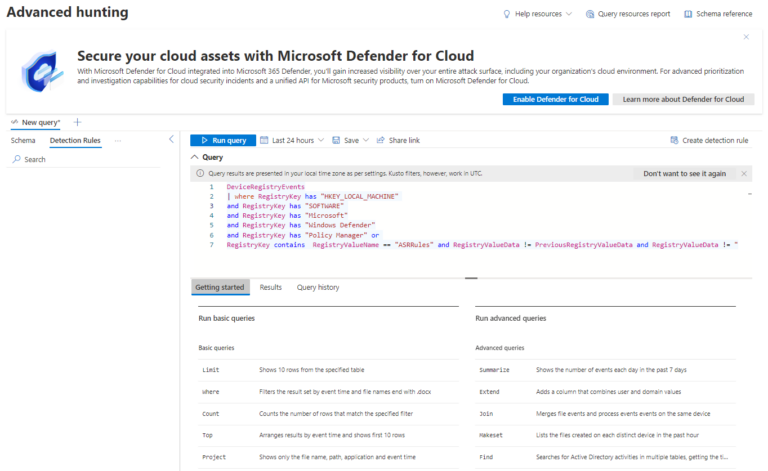
DeviceRegistryEvents
| where RegistryKey has “HKEY_LOCAL_MACHINE”
and RegistryKey has “SOFTWARE”
and RegistryKey has “Microsoft”
and RegistryKey has “Windows Defender”
and RegistryKey has “Policy Manager” or
RegistryKey contains RegistryValueName == “ASRRules” and RegistryValueData != PreviousRegistryValueData and RegistryValueData != “ [Enter your registry key value here] ”
Suggested configurations:
Frequency: Every hour
Impacted Entity: Device | Device ID
Actions: Run antivirus scan
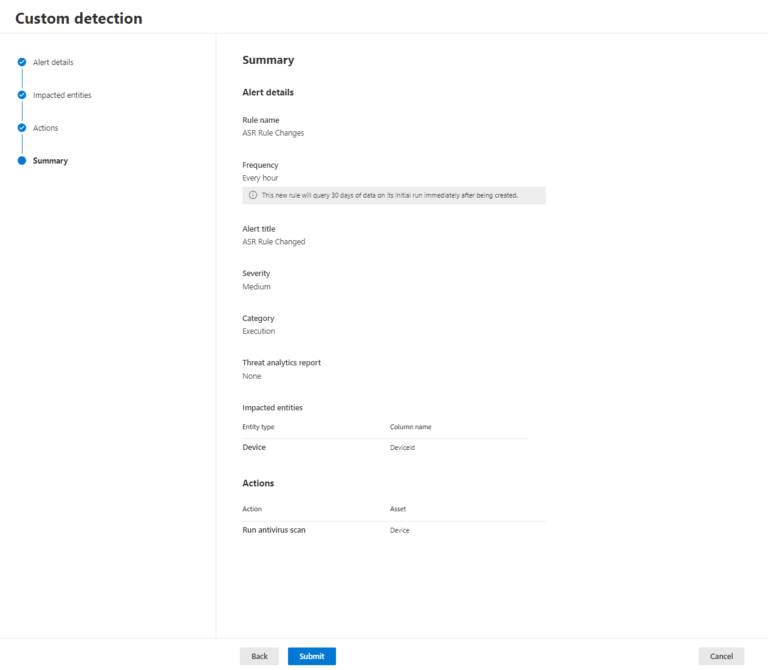
Once configured, the Custom detection rule will run once every hour and generate an alert for all devices in which the ASR rule registry key has changed.
Any alerts should be investigated as running a Microsoft Defender Antivirus scan alone will not be a sufficient response.
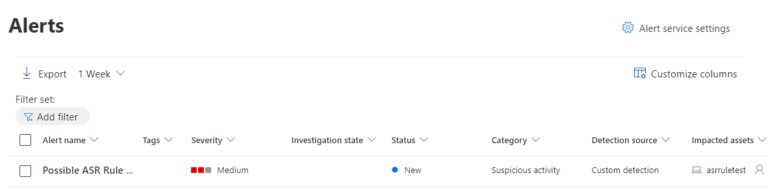
It is important to note that the registry key in the Advanced Hunting query should be updated after any change is made to the ASR rules.
By Neil du Plessis | Cloud Security Architect, BUI
Copilot for Microsoft 365 is an innovative tool that can transform how you work with computers. However, as with any new technology, it requires some preparation and adaptation on your part to ensure the most beneficial results in the long run.
Jared Spataro, the Corporate Vice President of Modern Work and Business Applications at Microsoft, once said that “becoming an AI-powered organisation doesn’t happen with the flip of a switch”. And he was right: you have to understand Copilot’s features and functionality before you can harness its full potential. Here are three important steps in the preparation journey.
Copilot is a powerful AI assistant that can help you with numerous tasks and activities in your Microsoft 365 apps, but it’s not a magic solution to every problem. You will need to learn how to use Copilot effectively – by composing clear prompts, providing relevant details and parameters, and reviewing and refining outputs.
You’ll also need to explore the frameworks guiding and controlling Copilot so that you understand how data security policies, privacy policies, and responsible AI checks are applied. Fortunately, there are plenty of resources available online, from technical documentation to in-depth tutorials and walkthroughs. You can also watch these introductory videos to see how Copilot for Microsoft 365 works:

Even though Copilot can help you augment your capabilities, it’s no substitute for your unique human intelligence. Remember that Copilot uses generative artificial intelligence to draft responses to your prompts, providing an output based on your input.
A well-structured, specific prompt with appropriate context will yield a more accurate result than a vague query. If you take the time to develop your prompt engineering skills and evaluate, analyse, and even interrogate Copilot’s output, you’ll be better prepared to use the tool properly.
It’s also essential to apply your professional judgement, ethical standards, and niche industry or domain knowledge to your tasks and projects with Copilot. After all, the tool doesn’t have the benefit of your personal experience, expertise, or emotion.
Copilot is designed to be your digital assistant. Your AI sidekick. Your know-a-lot companion in Excel, Outlook, PowerPoint, Teams, and Word. But there will be a learning curve at the beginning – for you and the tool.
Because Copilot learns from context and adapts over time, it may not generate perfect responses to your queries from the start. You’ll need to experiment with different prompts and fine-tune your inputs to get high-quality outputs, so keep practising.
It’s also a good idea to join an online forum or community group of fellow Copilot users in your industry to take advantage of their shared knowledge, resources, and tips for success. The Copilot for Microsoft 365 community on the Microsoft Tech Community website is filled with news updates, event details, and discussions related to Copilot for Microsoft 365.
Learning how to use Copilot effectively, developing your prompt engineering and critical thinking skills, and tapping into the knowledge of fellow Copilot users can help you prepare for a new world of work with this AI-powered helper by your side.
BUI Cloud Security Architect Neil du Plessis is a certified CISSP and Microsoft Cybersecurity Expert specialising in holistic, cloud-powered defences for modern workplaces.
Wondering if Copilot for Microsoft 365 is right for your organisation? Join the BUI team for an interactive workshop and we’ll assess your Copilot for Microsoft 365 readiness and define a road map for your adoption journey. The workshop is conducted virtually, and is suitable for senior business development managers, line-of-business leaders, managers, technical decision-makers, and end-users. Register your interest by completing this digital form and we’ll contact you directly.
By Neil du Plessis | Cloud Security Architect, BUI
More than three-quarters of early users said that once they tried Copilot for Microsoft 365, they didn’t want to give it up. Why? Because having this AI-powered assistant as their workplace aide helped them to save time, unleash their creativity, enhance their skills, and unlock the full potential of their favourite Microsoft 365 apps.
In the Work Trend Index Special Report published by Microsoft last year, the same early users said that Copilot for Microsoft 365 empowered them to do more – and do it more efficiently than before. From creating presentations in PowerPoint to managing emails in Outlook, Copilot helped them achieve their goals.
But how exactly can Copilot for Microsoft 365 help you and your teams? How can you take advantage of this technology in your business right now? Let’s explore three everyday use cases for Copilot for Microsoft 365 in the modern workplace.
Whether you need to write a blog post, a newsletter, a proposal, or a summary, Copilot can help you with the creative process.
You can tell Copilot to draft an outline, a title, a hook, or a conclusion for your document based on your topic and purpose. You can get Copilot to check your grammar and spelling and edit, rewrite, or paraphrase your text to improve the tone, style, and clarity.
You can also direct Copilot to help you with formatting, referencing, and citing your sources so that your entire document is eye-catching, precise, and correctly attributed.
With Copilot as your co-creator, you can speed up the writing process and craft compelling content that meets your needs. Watch these videos for a closer look at what’s possible with Copilot in Word.
Whether you need to work with numbers, charts, tables, or graphs, Copilot can help you with data analysis and presentation.
You can get Copilot to perform calculations, apply formulas, filter data, or create pivot tables in Excel, based on your data set and goal.
You can ask Copilot to help you interpret and make sense of your data by providing summaries, trends, or insights in natural language.
You can also use Copilot to generate charts and graphs so that you can visualise your data, highlight relevant information, and vividly present your findings.
With Copilot by your side in Excel, you can enhance the way you work with and analyse data. Watch these videos to see how Copilot filters, formats, and reviews data.
Whether you need to plan a project, schedule a meeting, or follow up on an email, Copilot can help you with task management and day-to-day organisation.
You can ask Copilot to create a project plan, a timeline, or a checklist in Word, Excel, or PowerPoint, based on your project scope and deliverables.
You can instruct Copilot to schedule a meeting, send an invitation to your chosen attendees, and create an agenda to match the meeting topic – all from within Outlook or Teams.
You can also get Copilot to help you respond to emails, create tasks, and set reminders in Outlook or Teams, based on your email content and priorities.
With Copilot as your digital assistant, you can stay on top of your tasks and organise your calendar more efficiently. Watch these videos for an overview of Copilot’s functionality in Outlook and Teams.
Real-time intelligent assistance from Copilot for Microsoft 365 enables people to work more creatively and productively. More than 80% of surveyed users said Copilot makes it easier to get started on a first draft; take action after a meeting; and catch up on what they missed. More than 70% said Copilot helped them complete work faster and save time on mundane tasks. And 68% said Copilot improved the quality of their work.
Going forward, those who embrace Copilot for Microsoft 365 as an ally at work and take the time to build new digital habits will benefit the most from this powerful technology.
BUI Cloud Security Architect Neil du Plessis is a certified CISSP and Microsoft Cybersecurity Expert specialising in holistic, cloud-powered defences for modern workplaces.
Wondering if Copilot for Microsoft 365 is right for your organisation? Join the BUI team for an interactive workshop and we’ll assess your Copilot for Microsoft 365 readiness and define a road map for your adoption journey. The workshop is conducted virtually, and is suitable for senior business development managers, line-of-business leaders, managers, technical decision-makers, and end-users. Register your interest by completing this digital form and we’ll contact you directly.
By Neil du Plessis | Cloud Security Architect, BUI
Copilot for Microsoft 365, the advanced AI assistant embedded in Microsoft 365 apps like PowerPoint and Word, made waves in workplaces worldwide after it was ANNOUNCED IN 2023.
The tool enables people to perform tasks and generate content using natural language commands and is ALREADY CONSIDERED A GAME-CHANGER for productivity and human-computer interaction, even as Microsoft continues to refine its capabilities and features.
So, what can we expect from this innovative technology going forward? Here are four important updates to know about Copilot for Microsoft 365.
On 1 November last year, Microsoft made Copilot for Microsoft 365 available to Microsoft 365 customers on Enterprise plans. Since then, Microsoft has removed the Microsoft 365 prerequisite and minimum-purchase restrictions to expand its Copilot for Microsoft 365 licensing model to include enterprises using Office 365 E3/E5 and small and medium-sized businesses (SMBs).
As of 15 January 2024, Enterprise customers (Office 365 E3, Office 365 E5, Microsoft 365 E3 and Microsoft 365 E5) and Business customers (Microsoft 365 Business Standard and Microsoft 365 Business Premium) can purchase Copilot for Microsoft 365 as an add-on to an existing subscription for $30 per user per month.
Initially, Copilot was only available in English for users based in the United States, Canada, and the United Kingdom. Today, it’s available in 36 regions across the Americas, Europe, Africa, and Asia, and Microsoft is working hard to expand both audience and market reach.
In addition to English, Copilot for Microsoft 365 is supported in Chinese (Simplified), French, German, Italian, Japanese, Portuguese, and Spanish. Microsoft plans to support several more languages over the first half of 2024, including Arabic, Chinese (Traditional), Czech, Danish, Dutch, Finnish, Hebrew, Hungarian, Korean, Norwegian, Polish, Russian, Swedish, Thai, Turkish, and Ukrainian.

Microsoft is enhancing the workplace value of Copilot for Microsoft 365 by adding new features and integrating it with more apps and services – both inside and outside of the Microsoft 365 suite. For example, Copilot works seamlessly with Loop and SharePoint, and is coming soon in Planner, OneNote, and Stream to allow users to access and manage files and tasks through natural language prompts and queries.
Copilot can also connect with third-party apps and services, including Salesforce, Jira, Dynamics 365, Bing Web Search, ServiceNow, and Zendesk, enabling users to perform actions and gather external information without leaving their current app.
Copilot can also leverage the power of the Microsoft Graph and third-party integrated applications like SQL and Confluence to provide users with personalised, contextual suggestions and insights based on their preferences, history, and activity.
Microsoft is committed to improving Copilot for Microsoft 365 so that it consistently produces relevant, high-quality output for users based on their prompts and context. To achieve this, Microsoft has been refining Copilot’s processing and orchestration engine, updating its Large Language Models, and gathering public and partner feedback through early access programmes, preview programmes, and dedicated community forums like the Copilot Feedback Hub, where users can share their observations, suggestions, and experiences with the tool.
These efforts continue to yield results: Copilot’s accuracy and reliability have improved significantly since launch; 70% of early users have reported increased personal productivity; and 77% of early users have said that once they used Copilot, they didn’t want to give it up.
With its expanded licensing model, broader language support, increased integration with apps and services, and improved accuracy and reliability, Copilot for Microsoft 365 is set to become a critical tool for businesses of all sizes.
As Microsoft further refines Copilot’s capabilities and features, we can expect this AI-powered assistant to revolutionise organisations everywhere by empowering people to do more with their favourite Microsoft 365 apps every day.
BUI Cloud Security Architect Neil du Plessis is a certified CISSP and Microsoft Cybersecurity Expert specialising in holistic, cloud-powered defences for modern workplaces.
Wondering if Copilot for Microsoft 365 is right for your organisation? Join the BUI team for an interactive workshop and we’ll assess your Copilot for Microsoft 365 readiness and define a road map for your adoption journey. The workshop is conducted virtually, and is suitable for senior business development managers, line-of-business leaders, managers, technical decision-makers, and end-users. Register your interest by completing this digital form and we’ll contact you directly.
By Paul Wallett | National Sales Manager, BUI
Broadcom’s acquisition of VMware in November 2023 ignited a fierce debate within the technology community. While some applauded the $69-billion deal as a strategic move to streamline operations and simplify the virtualisation and cloud computing market, others voiced concern about its effects on VMware’s products and customers. In the short time since the takeover, there have been significant developments that VMware users and the IT industry now need to navigate.
I’ve used VMware solutions myself and have seen firsthand how they can enhance business efficiency, agility, and innovation through virtualisation and cloud technology. With products like VMware SD-WAN and VMware SASE consistently acknowledged for being reliable and able to cater to organisations with diverse infrastructure and operational requirements, it’s no surprise that VMware’s portfolio has been a popular choice for so many businesses and enterprises for so long.
However, since Broadcom assumed control of VMware, the VMware product landscape has been transformed, with two key announcements directly impacting existing customers.
Firstly, Broadcom’s introduction of a subscription-only model for most VMware products is a sea change for customers who have traditionally favoured perpetual licences. The shift eliminates the option of perpetual licences, potentially disrupting customers’ long-term investment planning and leading to higher costs in the form of recurring subscription fees.
Secondly, Broadcom’s decision to discontinue 56 standalone VMware products – including flagship offerings like vSphere, vSAN, and NSX – has roiled VMware customers worldwide. For countless organisations, these products are the backbone of core IT functions such as virtualisation, storage, and networking. Their discontinuation has left customers scrambling for alternatives and grappling with the gruelling task of migrating to other platforms.
Beyond the immediate concerns for customers, Broadcom’s acquisition of VMware has wide-ranging implications for the technology industry.
VMware’s virtualisation and cloud computing leadership fostered a vibrant ecosystem of partners, resellers, and service providers. However, Broadcom’s restructuring efforts – including the termination of partner agreements and the introduction of an invitation-only partner programme – have disrupted these relationships, causing waves of uncertainty within the IT industry.
Furthermore, Broadcom’s focus on maximising revenue from enterprise customers risks alienating loyal small and medium-sized businesses (SMBs) and managed service providers (MSPs). The transition to subscription-based licensing models and the discontinuation of key VMware products may impact SMBs and MSPs disproportionately, limiting their access to VMware’s technologies and services and prompting them to look elsewhere for similar IT solutions.
As Broadcom continues to reshape VMware with streamlining initiatives and new product plans, customers will face more turbulent waters. Those who navigate the stormy conditions with care will emerge stronger. And fortunately, they don’t have to brave such challenges alone: BUI remains steadfast in its commitment to help people thrive in the evolving world of virtualisation and cloud computing.
From crafting tailored migration strategies to implementing robust cybersecurity measures and optimising network performance, BUI offers comprehensive solutions to enable performance and productivity in the digital era. Our expert technologists can provide the guidance and support that customers require as they adapt to Broadcom’s VMware changes.
If you’re wondering what’s next for your VMware technology stack, trying to make sense of the revamped licensing environment, or thinking about alternative virtualisation solutions, then contact BUI today. We can evaluate your IT setup, take stock of what you have and what you need, and identify the best resources for your particular goals. With a trusted technology partner like BUI on your side, you can confidently chart a course for the future and get back to business as usual.
BUI National Sales Manager Paul Wallett has 20+ years of experience in the technology industry and an extensive background in business development, sales management, and operations management.
By Zandre Janse van Vuuren | Service Delivery Manager: Cyber DFIR, BUI
Cybercrime has become more sophisticated, more frequent, and more damaging than ever, with companies falling victim to data breaches, ransomware scams, and other types of cyberattacks that often result in substantial financial losses and reputational damage. In the aftermath, they’re turning to Digital Forensics and Incident Response specialists to find answers – and to help them strengthen their security posture and avoid a repeat incident.
Digital Forensics and Incident Response (DFIR) is a niche field within cybersecurity that concentrates on identifying, preserving, analysing, and recovering digital information to investigate and respond to security incidents and cybercrimes.
DFIR specialists play a critical role in mitigating cyber threats and maintaining the integrity of connected digital systems. Their key focus areas typically include Incident Response, Digital Forensics, Analysis, Recovery, and Reporting.
DFIR specialists are responsible for quickly identifying and responding to security incidents like network intrusions, data breaches, malware infections, and cyberattacks. Their primary goal is to minimise the damage caused by the incident and prevent further unauthorised access by the perpetrator.
DFIR teams use sophisticated tools and investigative techniques to gather and analyse digital evidence from various sources, including servers, computers, portable drives, smart devices, mobile phones, and network logs. They must follow strict collection procedures and maintain a chain of custody to preserve the integrity of digital evidence so that it is admissible in any legal proceedings related to the incident.
DFIR teams thoroughly examine all digital evidence to uncover the scope of the incident and identify the perpetrator’s methods and motives. They also evaluate the extent of the damage caused to the victim’s connected environment by analysing logs, file systems, memory data, and network traffic, among other things.
DFIR specialists have advanced technology and security skills and can work to recover data, systems, or services lost or compromised due to the incident. This process may involve restoring backups, removing malware, and implementing new, more comprehensive security measures to reduce the victim’s attack surface in the future.
DFIR specialists are responsible for documenting their findings and preparing detailed technical and forensic reports suitable for legal purposes, regulatory compliance, or internal investigations. They can also appear in court as expert witnesses.
Last year, the average cost of a data breach was $4.45-million. Researchers estimate that cyberattacks will cost the global economy $10.5-trillion by the end of 2024. And by 2025, lack of skill or human failure will be responsible for more than half of significant security incidents.
It’s clear that cybercriminals are taking advantage of a perfect storm: our hyperconnected digital world, the global shortage of security professionals, readily available hacking tools, and the relative ease of operating anonymously on the web. In this volatile climate, you have to go beyond protecting and defending your IT environment and plan for when disaster strikes.
If you do not have an in-house team of DFIR experts to identify and contain threats, mitigate the impact of security incidents, and conduct in-depth investigations, then you should consider opting for a DFIR-as-a-Service solution. This will enable you to leverage the expertise of a trusted security partner and enjoy the five main benefits of DFIR-as-a-Service.
DFIR-as-a-Service partners usually have a team (or teams) of security professionals specialising in incident response and digital forensic investigation. These experts have cutting-edge skills and a wealth of experience gained from working on DFIR cases involving business and enterprise organisations in diverse industries. As a customer, you can tap into a much broader knowledge base than your company’s own and take advantage of the insights and lessons learned by these pros.
Every second counts when you’re dealing with a security incident. DFIR-as-a-Service partners are prepared to respond quickly when called upon. They have established procedures and playbooks to deal with the incident, and defined service-level agreements governing their engagements with you. As a result, you can expect swift incident analysis and containment, proper incident management, and dedicated support from DFIR experts – all crucial elements for minimising the impact of the incident.
DFIR-as-a-Service partners invest in cutting-edge tools to give their teams advanced incident response and digital forensic analysis capabilities. They also harness their relationships with technology peers, think tanks, and research institutions to gain deeper insights into the evolving threat landscape. As a customer, you can benefit from specialised technologies and sophisticated industry research without ever having to source these independently.
DFIR-as-a-Service partners are external parties who provide objective assistance and an outsider’s perspective on your security posture and any incidents. As DFIR experts, they are equipped to ensure that all digital forensic investigations are conducted thoroughly and impartially in compliance with legal and regulatory requirements. You can rest assured every incident will be handled responsibly, professionally, and with complete transparency.
Creating and managing an in-house DFIR team is a costly and time-consuming process. It involves finding and training DFIR professionals and procuring state-of-the-art hardware and software – all of which can strain your budget. On the other hand, when you hire a DFIR-as-a-Service partner, you instantly broaden your organisation’s DFIR capabilities without having to bear the overhead costs associated with maintaining a full-time internal team.
As cybercrime continues to evolve at an unprecedented pace, the importance of Digital Forensics and Incident Response cannot be overstated. If you’re serious about holistic protection for your organisation, then a robust DFIR strategy is not just advisable – it’s imperative.
A DFIR-as-a-Service solution customised for your company is a proactive investment in security that will give you the peace of mind that comes with knowing you have a team of specialists on standby to help you safeguard your assets, protect your reputation, and preserve business continuity in challenging times.
BUI Cyber DFIR Service Delivery Manager Zandre Janse van Vuuren is a certified computer, digital and mobile forensics specialist and incident handler with a background in security operations.
Call in our security and digital forensics experts when it matters most. From lone attackers to ransomware groups, cyberspace is filled with adversaries. Solid preparation is essential. Our Cyber DFIR team can provide all the support you need in times of crisis. Learn more about our Digital Forensics and Incident Response retainer service, available now.
BUI announced its commitment to Data Privacy Week 2024 by registering as a Champion. As a Champion, BUI recognises and supports the principle that all organisations share the responsibility of being conscientious stewards of personal information. Data Privacy Week is an annual expanded effort from Data Privacy Day – taking place from 21st – 27th of January 2024. The goal of Data Privacy Week is to spread awareness about online privacy among individuals and organisations. The goal is twofold: to help citizens understand that they have the power to manage their data and to help organisations understand why it is important that they respect their users’ data.
The US National Cybersecurity Alliance (NCA) recommends adopting the following market leading practices:
Remember that most employees aren’t privacy or security experts. You will need to build in mechanisms that make it easy for them to report privacy and security concerns to your experts. Just like tools for preventing privacy incidents are critical, tools that easily empower employees to report are necessary in your company’s privacy toolbox, too.
Outsourcing to professional cybersecurity companies takes a load off your plate and ensures you have the data protection you deserve.
All your online activity generates a trail of data. Websites, apps, and services collect data on your behaviours, interests, and purchases. Sometimes, this includes personal data, like your Social Security and driver’s license numbers. It can even include data about your physical self, like health data – think about how a smartwatch counts and records how many steps you take.
While it’s true that you cannot control how each byte of data about you and your family is shared and processed, you are not helpless! In many cases, you can control how you share your data with a few simple steps. Remember, your data is precious, and you deserve to be selective about who you share it with!
Follow these steps to better manage your personal information and make informed decisions about who receives your data.
Data Privacy Week began as Data Privacy Day in the United States and Canada in January 2008 as an extension of the Data Protection Day celebration in Europe. Data Protection Day commemorates the 28th of January 1981, signing of Convention 108, the first legally binding international treaty dealing with privacy and data protection. NCA, the nation’s leading nonprofit, public-private partnership promoting cybersecurity and privacy education and awareness, leads the effort in North America each year.
For more information, visit https://staysafeonline.org/data-privacy-week/.
The National Cybersecurity Alliance is a non-profit organisation on a mission to create a more secure, interconnected world. We advocate for the safe use of all technology and educate everyone on how best to protect ourselves, our families, and our organisations from cybercrime. We create strong partnerships between governments and corporations to amplify our message and to foster a greater “digital” good.
For more information about Data Privacy Week and how to get involved, visit https://staysafeonline.org.
Cybercriminals are targeting enterprises big and small to try to gain access to sensitive, confidential, or proprietary data and resources.
How are you protecting your IT environment? Stay ahead of threat actors by choosing a managed detection and response service from BUI.
BUI has been recognised as a Microsoft Azure Expert Managed Services Provider (MSP) for the fourth year in a row!
“When we first achieved Azure Expert MSP status in 2020, it was a significant accomplishment for our company and a key milestone in our longstanding relationship with Microsoft,” says Ryan Roseveare, our Global CEO. “Since then, we have diversified our range of cloud solutions to help customers leverage the speed, scale, and security of Azure to enable innovation and sustainable growth in their own businesses.”
“We are thrilled to have renewed our Azure Expert MSP certification for the fourth consecutive year,” continues Roseveare. “As the premier Azure designation for Microsoft partners, this accreditation is an acknowledgement of the depth and breadth of our cloud-management capabilities and our commitment to maintaining the highest standards of customer service.”
Microsoft launched the Azure Expert MSP programme in 2018 as a way to showcase the most skilled and capable Azure managed services providers. To participate in the programme, Microsoft partners must pass an independent audit of their people, processes, and technologies – and prove that they can deliver high-fidelity Azure managed services and world-class technical support to customers. BUI was evaluated in September this year.
“We underwent an intensive third-party review of our teams, our Azure methodologies and frameworks, our competencies, our corporate performance, our customer successes, and much more,” explains Dhiren Boodhia, our Group Governance and Compliance Manager. “These annual audits are always in-depth, but this year’s assessment was particularly comprehensive – and we excelled in all areas. We are delivering outstanding work for our customers and this Azure Expert MSP re-certification is a testament to the passion and dedication of everyone here,” says Boodhia.
Willem Malan, our Chief Technology Officer, agrees. “There are more than 400 000 Microsoft partner organisations around the world and only 132 of them are currently certified as Azure Expert MSPs.
Globally, BUI is in the top tier of Microsoft partners with the necessary expertise and experience to design, deploy, manage, secure, and optimise business solutions on Azure,” says Malan. “Whether it’s a straightforward lift-and-shift migration or a complex digital transformation project, we can support customers at every stage of their Azure journey, and beyond.”
In addition to our credentials as an Azure Expert MSP and Microsoft Solutions Partner for Microsoft Cloud, we’re proud to be a Microsoft Security Experts MXDR Partner, a member of the prestigious Microsoft Intelligent Security Association, and a three-time Microsoft Country Partner of the Year holding 10 Microsoft Advanced Specializations including Cloud Security, Infra and Database Migration to Microsoft Azure, and Microsoft Azure Virtual Desktop.
“We have earned our standing as Azure experts because we’ve invested in our people, our business, and our relationship with Microsoft,” continues Malan. “We’re enabling our cloud teams to develop cutting-edge technical skills. We’re expanding into new markets. And we’re working closely with Microsoft as the cloud landscape changes. We’re doing all of this to ensure that our customers continue to receive the best possible advice and support – and the right Azure solutions for their business needs.”
The BUI Cloud Centre of Excellence (CCoE) plays an important role in this regard, notes our governance and compliance head. “The Azure administrators, architects, consultants, developers, engineers, and security specialists in our CCoE are Microsoft certified professionals adept in the principles of the Microsoft Cloud Adoption Framework. We follow Microsoft’s established codes, guidelines, and best practices on every Azure project to make sure that our customers’ connected environments are well-managed and fully optimised for performance, security, and compliance,” says Boodhia.
Re-certification as an Azure Expert MSP validates our exceptional cloud-management capabilities and gives our current and future customers peace of mind, says chief executive Roseveare. “With more than two decades of success in the technology sector, a global footprint, and verified Azure experts specialising in everything from cloud infrastructure to cloud security, BUI is a trusted Microsoft partner equipped to deliver impactful results and real value for business organisations from Day 1, and every day thereafter. We look forward to our continued collaboration with Microsoft, and to helping our mutual customers achieve more with Azure,” Roseveare concludes.
From foundational support and monitoring to full-scale management and continuous optimisation, our cloud experts are here to help you achieve more with Azure.
BUI is proud to participate in Cyber Security Awareness Month as a Champion Organisation for the sixth consecutive year. Founded in 2004, Cyber Security Awareness Month (held each October) is the world’s foremost initiative aimed at promoting cyber security awareness and best practices. The campaign is a collaborative effort among businesses, government agencies, colleges and universities, associations, non-profit organisations, communities and individuals to educate others about online safety.
“Knowledge and vigilance are essential when it comes to cyber security,” says BUI Global CEO Ryan Roseveare. “You need to know what to look out for. You need to know what to do when you see a red flag. And you need to be alert whenever you’re online. Cyber Security Awareness Month plays a key role in educating the public about common cyber risks and encouraging everyone to become more vigilant. BUI is pleased to join the international community in this focused effort to improve cyber security awareness worldwide.”
From smartphones to web-enabled home devices, technology is deeply intertwined with our lives. And while the evolution of technology accelerates, cybercriminals are working just as hard to find ways to compromise technology and disrupt our personal and business activities.
Cyber Security Awareness Month aims to highlight some of the emerging challenges that exist in the world of cyber security today and provide straightforward, actionable guidance which anyone can follow to create a safer, more secure digital world for themselves and their loved ones.
Starting this year, the new theme of Cyber Security Awareness Month is Secure Our World. The main messaging revolves around four cyber security practices:
For more information about the 2023 Cyber Security Awareness Month campaign, you can visit the CISA and Stay Safe Online websites. You can also follow BUI on LinkedIn, Facebook and X (formerly Twitter) for helpful tips and resources throughout October, and join the global conversation by including the hashtag #CyberSecurityAwarenessMonth in your own social media posts.
Cybercriminals are targeting enterprises big and small to try to gain access to sensitive, confidential, or proprietary data and resources. How are you protecting your IT environment?
Stay ahead of threat actors by choosing a comprehensive managed extended detection and response service from BUI. Contact our team to explore Cyber MXDR today.