Terms and Conditions for this security vulnerability disclosure blog:
Microsoft Defender XDR is a comprehensive cybersecurity solution designed by Microsoft to protect organisational networks and devices. At its core are the Attack Surface Reduction (ASR) rules, which are strategic security protocols aimed at minimising the vulnerabilities and pathways exploited by cyber threats. These rules act as a crucial line of defence, shielding endpoints from various attack vectors such as malicious documents, scripts, and other potentially harmful activities. However, despite their importance in fortifying cybersecurity defences, recent scrutiny has uncovered a critical vulnerability within these ASR rules. This vulnerability poses a significant risk as it allows adversaries to bypass established security measures without triggering alerts or raising suspicion, thereby compromising the effectiveness of Microsoft Defender XDR’s defence mechanisms.
Regrettably, a remedy for this issue is not yet available*. Consequently, recourse to Advanced Hunting queries armed with Custom detection rules becomes imperative to diligently monitor for any indicators of compromise, thereby mitigating potential risks.
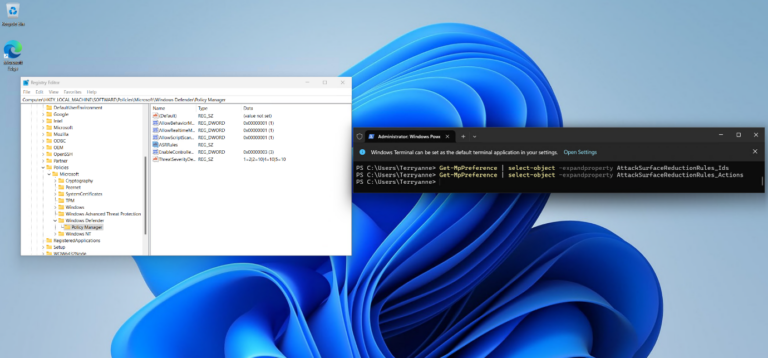
Attack Surface Reduction (ASR) rules are configured on devices by means of a registry key. The contents of this key include the GUID for the specific ASR rule as well as the state of the rule (Block, Audit).
The registry key is not protected and can be modified without triggering any alerts, essentially bypassing ASR rules, which could result in negation of the protection.
Registry Key:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Policy Manager\ASR Rules
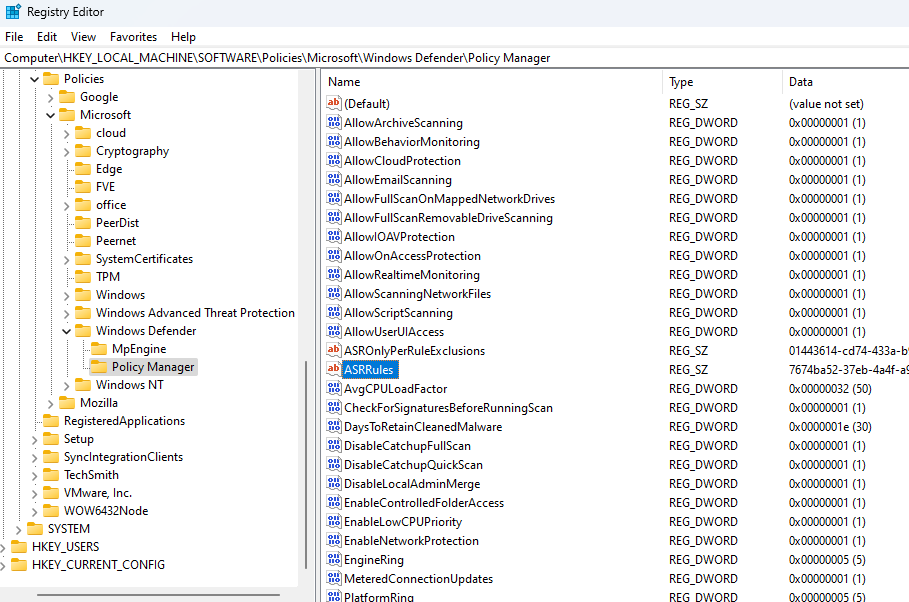
By following the steps below, ASR rules can be bypassed. The rule Block all Office applications from creating child processes will be tested.
Bypassing ASR rules:
Get-MpPreference | Select-Object -expandproperty AttackSurfaceReductionRules_Ids
Get-MpPreference | Select-Object -expandproperty AttackSurfaceReductionRules_Actions
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Policy Manager\
ASR Rules
Get-MpPreference | Select-Object -expandproperty AttackSurfaceReductionRules_Ids
Get-MpPreference | Select-Object -expandproperty AttackSurfaceReductionRules_Actions
Testing the bypass:
Example: Mkdir “c:\tools\new folder”
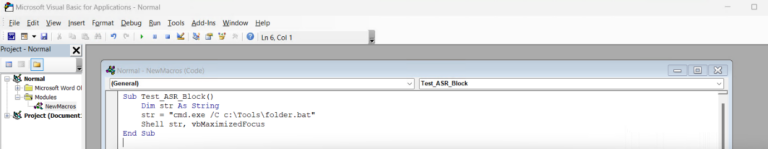
Sub [your Macro name] ()
Dim str As String
Str = “cmd.exe /C [location of bat file] ”
shell str, vbMaximizedFocus
End Sub
Example shown here in screenshot:
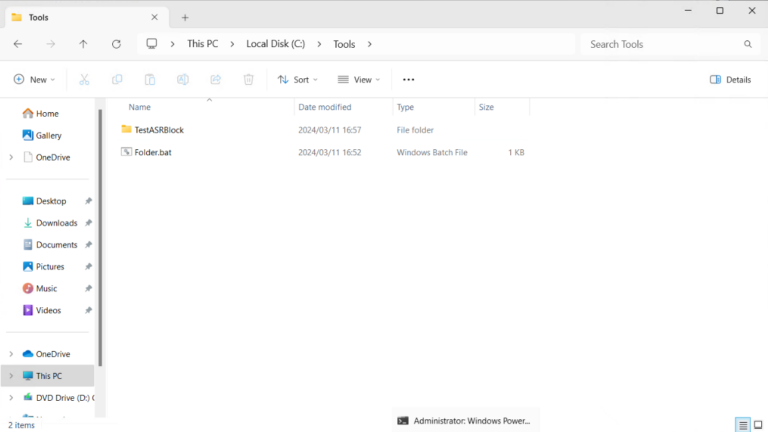
The successful creation of a folder indicates that ASR rules have been successfully bypassed.
Running the same Macro without bypassing the ASR rules results in the following alert:
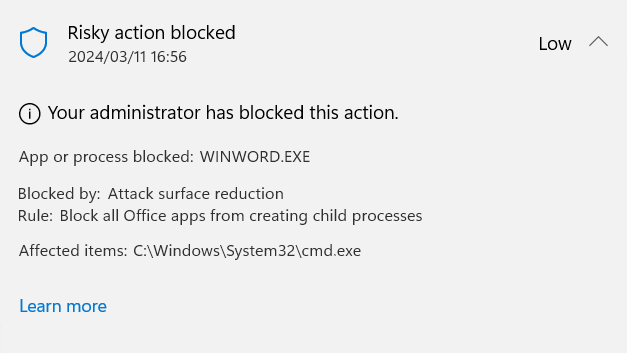
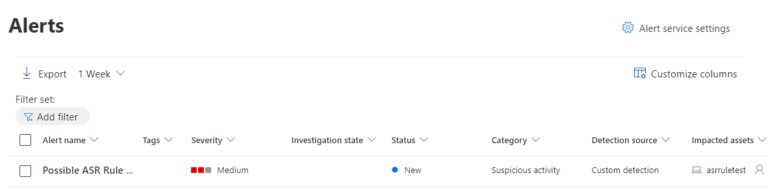
By determining the current ASR policy configuration and monitoring for any changes to this configuration, Advanced Hunting queries with Custom detection rules can act as a potential mitigation strategy until this critical vulnerability is remediated.
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Policy Manager\ASR Rules
DeviceRegistryEvents
| where RegistryKey has “HKEY_LOCAL_MACHINE”
and RegistryKey has “SOFTWARE”
and RegistryKey has “Microsoft”
and RegistryKey has “Windows Defender”
and RegistryKey has “Policy Manager” or
RegistryKey contains RegistryValueName == “ASRRules” and RegistryValueData != PreviousRegistryValueData and RegistryValueData != “ [Enter your registry key value here] ”
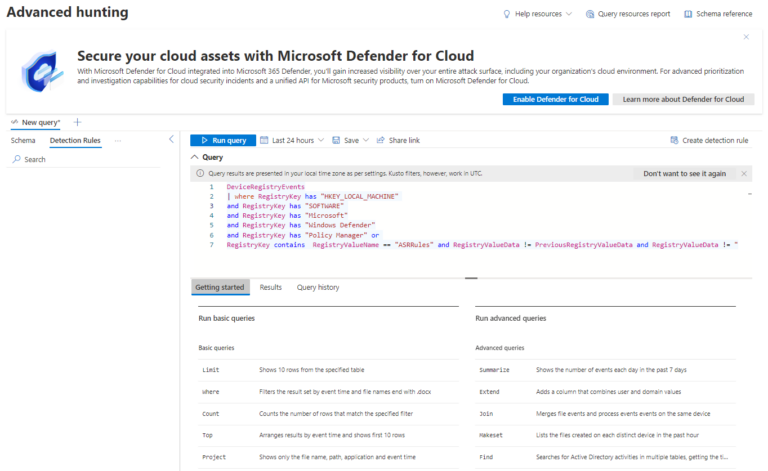
Suggested configurations:
Frequency: Every hour
Impacted Entity: Device | Device ID
Actions: Run antivirus scan
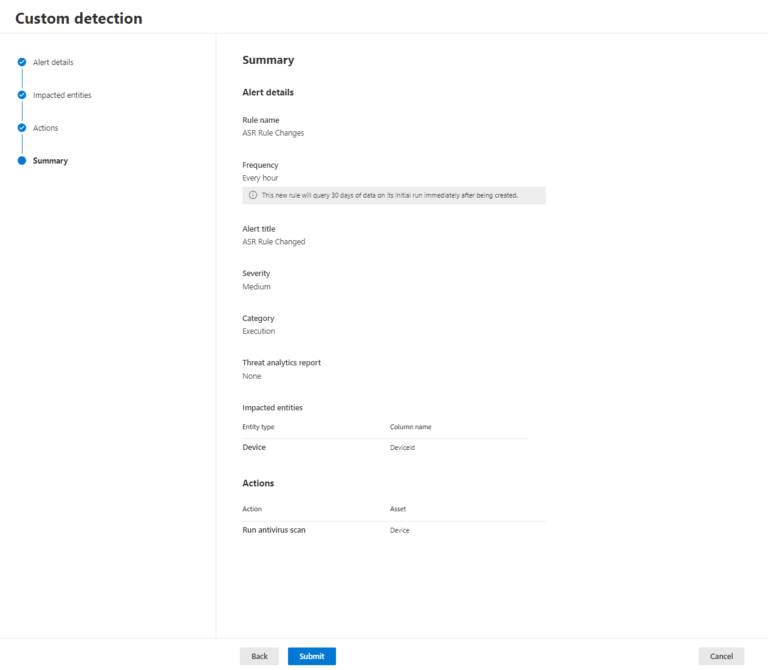
Once configured, the Custom detection rule will run once every hour and generate an alert for all devices in which the ASR rule registry key has changed.
Any alerts should be investigated as running a Microsoft Defender Antivirus scan alone will not be a sufficient response.
It is important to note that the registry key in the Advanced Hunting query should be updated after any change is made to the ASR rules.
BUI is proud to participate in Cyber Security Awareness Month as a Champion Organisation for the sixth consecutive year. Founded in 2004, Cyber Security Awareness Month (held each October) is the world’s foremost initiative aimed at promoting cyber security awareness and best practices. The campaign is a collaborative effort among businesses, government agencies, colleges and universities, associations, non-profit organisations, communities and individuals to educate others about online safety.
“Knowledge and vigilance are essential when it comes to cyber security,” says BUI Global CEO Ryan Roseveare. “You need to know what to look out for. You need to know what to do when you see a red flag. And you need to be alert whenever you’re online. Cyber Security Awareness Month plays a key role in educating the public about common cyber risks and encouraging everyone to become more vigilant. BUI is pleased to join the international community in this focused effort to improve cyber security awareness worldwide.”
From smartphones to web-enabled home devices, technology is deeply intertwined with our lives. And while the evolution of technology accelerates, cybercriminals are working just as hard to find ways to compromise technology and disrupt our personal and business activities.
Cyber Security Awareness Month aims to highlight some of the emerging challenges that exist in the world of cyber security today and provide straightforward, actionable guidance which anyone can follow to create a safer, more secure digital world for themselves and their loved ones.
Starting this year, the new theme of Cyber Security Awareness Month is Secure Our World. The main messaging revolves around four cyber security practices:
For more information about the 2023 Cyber Security Awareness Month campaign, you can visit the CISA and Stay Safe Online websites. You can also follow BUI on LinkedIn, Facebook and X (formerly Twitter) for helpful tips and resources throughout October, and join the global conversation by including the hashtag #CyberSecurityAwarenessMonth in your own social media posts.
Cybercriminals are targeting enterprises big and small to try to gain access to sensitive, confidential, or proprietary data and resources. How are you protecting your IT environment?
Stay ahead of threat actors by choosing a comprehensive managed extended detection and response service from BUI. Contact our team to explore Cyber MXDR today.